
Users are accessing resources from anywhere—across cloud, on-premises, and hybrid environments—expanding the attack surface. Identity attacks continue to rise, reinforcing the need to treat identity as a core security control.
Identity is the cornerstone of a Zero Trust strategy: organizations must determine who the user is (employee, guest, supplier, temporary worker), what access they should get, and apply a least-access policy that allows only the resources necessary for the role, with the ability to revoke access as needed.
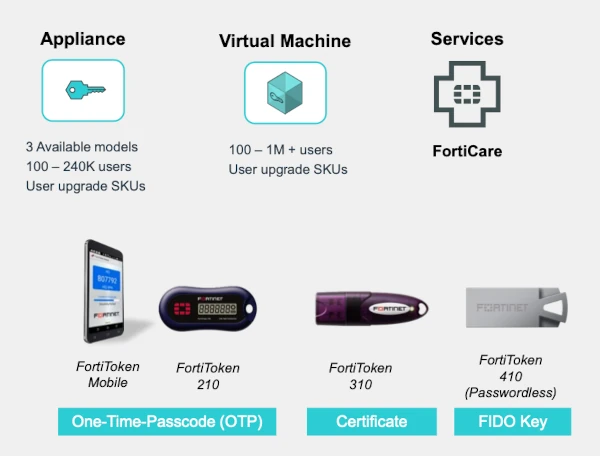
Identity-centric security aligns with the NIST Cybersecurity Framework to improve risk management and operates within the Fortinet Security Fabric platform alongside Secure Networking, Unified SASE, and AI-driven SecOps.
Taken together, these capabilities reinforce identity as the foundation for Zero Trust: verifying users, applying least-privilege access, and improving the overall security posture while keeping user experience manageable across hybrid environments.
Contact us for more information about the related products and solutions:
Toronto, ON. M9B 3E7